mirror of
https://github.com/go-gitea/gitea.git
synced 2025-11-04 15:04:00 +01:00
Co-Author: @silverwind @wxiaoguang Replace: #24404 See: - [defining configuration variables for multiple workflows](https://docs.github.com/en/actions/learn-github-actions/variables#defining-configuration-variables-for-multiple-workflows) - [vars context](https://docs.github.com/en/actions/learn-github-actions/contexts#vars-context) Related to: - [x] protocol: https://gitea.com/gitea/actions-proto-def/pulls/7 - [x] act_runner: https://gitea.com/gitea/act_runner/pulls/157 - [x] act: https://gitea.com/gitea/act/pulls/43 #### Screenshoot Create Variable: 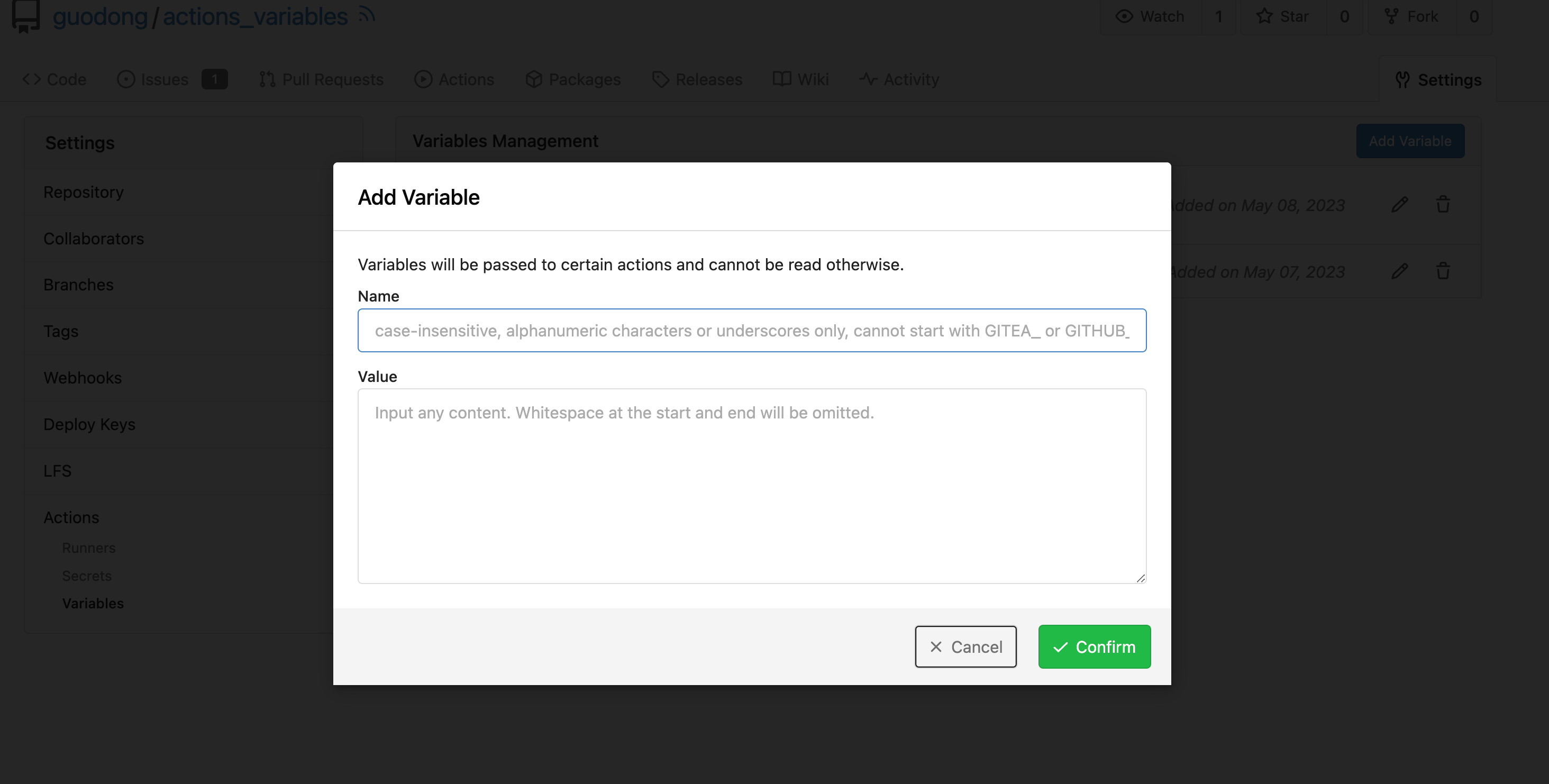 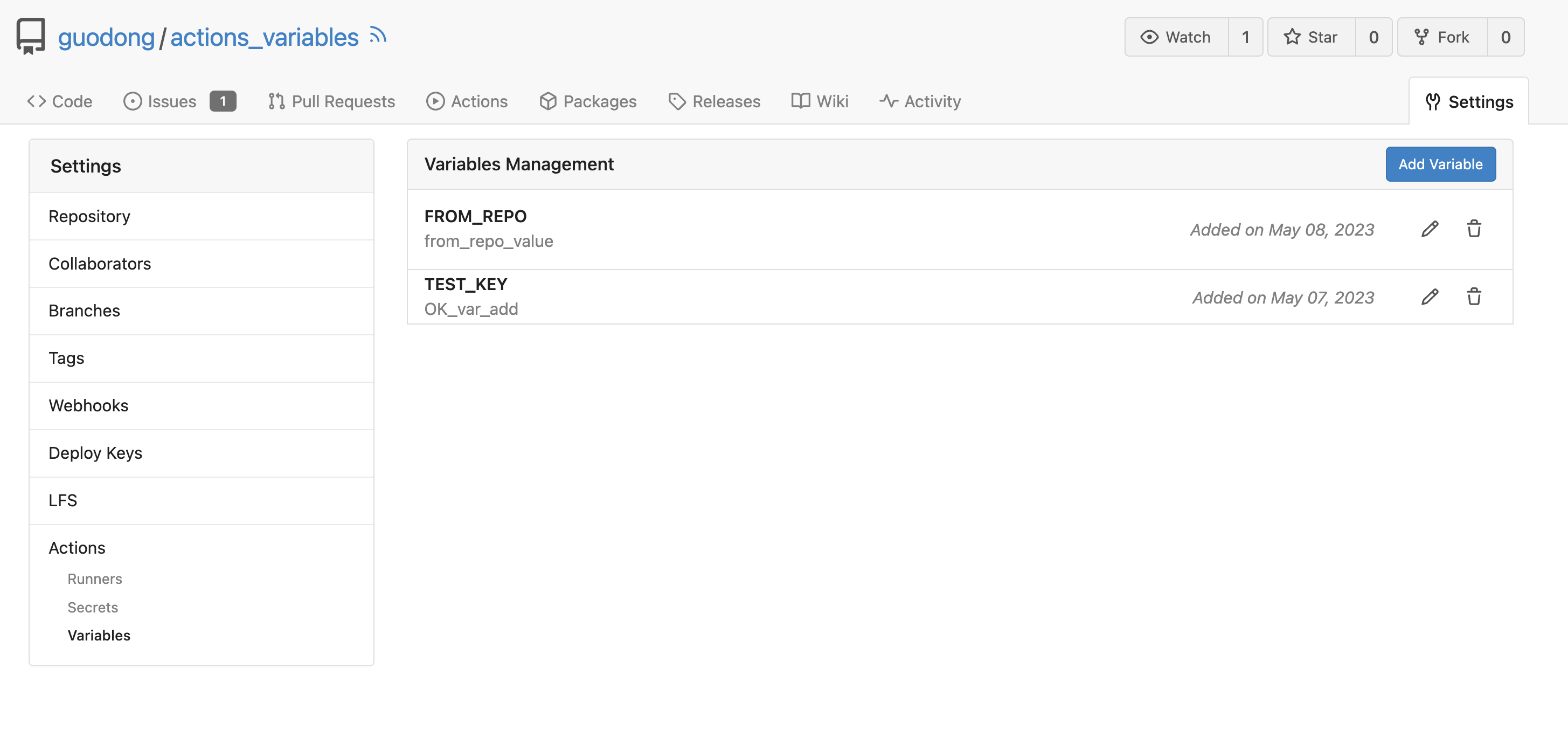 Workflow: ```yaml test_vars: runs-on: ubuntu-latest steps: - name: Print Custom Variables run: echo "${{ vars.test_key }}" - name: Try to print a non-exist var run: echo "${{ vars.NON_EXIST_VAR }}" ``` Actions Log:  --- This PR just implement the org / user (depends on the owner of the current repository) and repo level variables, The Environment level variables have not been implemented. Because [Environment](https://docs.github.com/en/actions/deployment/targeting-different-environments/using-environments-for-deployment#about-environments) is a module separate from `Actions`. Maybe it would be better to create a new PR to do it. --------- Co-authored-by: silverwind <me@silverwind.io> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com> Co-authored-by: Giteabot <teabot@gitea.io>
122 lines
2.6 KiB
Go
122 lines
2.6 KiB
Go
// Copyright 2022 The Gitea Authors. All rights reserved.
|
|
// SPDX-License-Identifier: MIT
|
|
|
|
package setting
|
|
|
|
import (
|
|
"errors"
|
|
"net/http"
|
|
|
|
"code.gitea.io/gitea/modules/base"
|
|
"code.gitea.io/gitea/modules/context"
|
|
"code.gitea.io/gitea/modules/setting"
|
|
shared "code.gitea.io/gitea/routers/web/shared/secrets"
|
|
)
|
|
|
|
const (
|
|
// TODO: Separate secrets from runners when layout is ready
|
|
tplRepoSecrets base.TplName = "repo/settings/actions"
|
|
tplOrgSecrets base.TplName = "org/settings/actions"
|
|
tplUserSecrets base.TplName = "user/settings/actions"
|
|
)
|
|
|
|
type secretsCtx struct {
|
|
OwnerID int64
|
|
RepoID int64
|
|
IsRepo bool
|
|
IsOrg bool
|
|
IsUser bool
|
|
SecretsTemplate base.TplName
|
|
RedirectLink string
|
|
}
|
|
|
|
func getSecretsCtx(ctx *context.Context) (*secretsCtx, error) {
|
|
if ctx.Data["PageIsRepoSettings"] == true {
|
|
return &secretsCtx{
|
|
OwnerID: 0,
|
|
RepoID: ctx.Repo.Repository.ID,
|
|
IsRepo: true,
|
|
SecretsTemplate: tplRepoSecrets,
|
|
RedirectLink: ctx.Repo.RepoLink + "/settings/actions/secrets",
|
|
}, nil
|
|
}
|
|
|
|
if ctx.Data["PageIsOrgSettings"] == true {
|
|
return &secretsCtx{
|
|
OwnerID: ctx.ContextUser.ID,
|
|
RepoID: 0,
|
|
IsOrg: true,
|
|
SecretsTemplate: tplOrgSecrets,
|
|
RedirectLink: ctx.Org.OrgLink + "/settings/actions/secrets",
|
|
}, nil
|
|
}
|
|
|
|
if ctx.Data["PageIsUserSettings"] == true {
|
|
return &secretsCtx{
|
|
OwnerID: ctx.Doer.ID,
|
|
RepoID: 0,
|
|
IsUser: true,
|
|
SecretsTemplate: tplUserSecrets,
|
|
RedirectLink: setting.AppSubURL + "/user/settings/actions/secrets",
|
|
}, nil
|
|
}
|
|
|
|
return nil, errors.New("unable to set Secrets context")
|
|
}
|
|
|
|
func Secrets(ctx *context.Context) {
|
|
ctx.Data["Title"] = ctx.Tr("actions.actions")
|
|
ctx.Data["PageType"] = "secrets"
|
|
ctx.Data["PageIsSharedSettingsSecrets"] = true
|
|
|
|
sCtx, err := getSecretsCtx(ctx)
|
|
if err != nil {
|
|
ctx.ServerError("getSecretsCtx", err)
|
|
return
|
|
}
|
|
|
|
if sCtx.IsRepo {
|
|
ctx.Data["DisableSSH"] = setting.SSH.Disabled
|
|
}
|
|
|
|
shared.SetSecretsContext(ctx, sCtx.OwnerID, sCtx.RepoID)
|
|
if ctx.Written() {
|
|
return
|
|
}
|
|
ctx.HTML(http.StatusOK, sCtx.SecretsTemplate)
|
|
}
|
|
|
|
func SecretsPost(ctx *context.Context) {
|
|
sCtx, err := getSecretsCtx(ctx)
|
|
if err != nil {
|
|
ctx.ServerError("getSecretsCtx", err)
|
|
return
|
|
}
|
|
|
|
if ctx.HasError() {
|
|
ctx.JSONError(ctx.GetErrMsg())
|
|
return
|
|
}
|
|
|
|
shared.PerformSecretsPost(
|
|
ctx,
|
|
sCtx.OwnerID,
|
|
sCtx.RepoID,
|
|
sCtx.RedirectLink,
|
|
)
|
|
}
|
|
|
|
func SecretsDelete(ctx *context.Context) {
|
|
sCtx, err := getSecretsCtx(ctx)
|
|
if err != nil {
|
|
ctx.ServerError("getSecretsCtx", err)
|
|
return
|
|
}
|
|
shared.PerformSecretsDelete(
|
|
ctx,
|
|
sCtx.OwnerID,
|
|
sCtx.RepoID,
|
|
sCtx.RedirectLink,
|
|
)
|
|
}
|